Topics Map > Users Tab
KB User's Guide - Users Tab - Group Authorization
- Creating an Authorized Group
- Rule Attributes
- Deleting Group Authorization Rules
- Other Considerations
Note
Adding these rules to your KB will not auto-populate the Active Users table in the KB Admin Tools. Should a member of your Group Authorization want to edit/ publish documents, please follow the instructions in this document to add a new user to your KB site.
Creating an Authorized Group
-
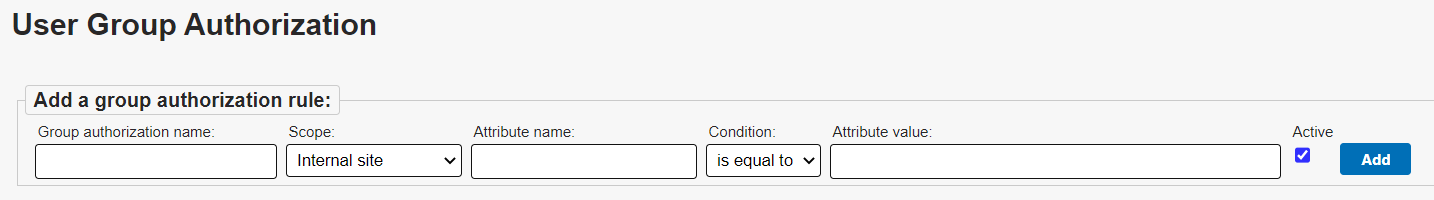
In the KB Admin Tools, go to the Users tab > Group Authorization link. The image below shows the User Group Authorization screen.

-
From the User Group Authorization screen, enter a Group authorization name. You can make the name whatever you want, but it should be descriptive enough that you can recognize its purpose when referenced elsewhere in the KB Admin Tools.
-
Specify the Scope from the dropdown list. You will have two options:
-
Internal site: Allows users that the meet the rule criteria to log in to the Internal Live KB site. These users will have the same level of access as a user account that has the "Internal KB" ("iKB") permission under the Users tab.
-
Document specific: The group will appear as a option under the WriteAccess and ReadAccess sections of the document editor screen. Users to whom the rule applies will gain read and/or write access to the documents associated with the group.
-
Note: For group-authorized WriteAccess to work, the user will first need to have a user account in your space with basic author permissions.
For group-authorized ReadAccess to work, the user will first need to have a user account in your space with Internal site access, or they need to meet the criteria for a separate "Internal site" scoped authorization rule.
-
-
-
Choose an Attribute name. Please see the Rule Attributes section for guidance on what attributes can be used.
-
Choose a Condition from the dropdown list (e.g. is equal to, starts with, contains, or is in)
- Note: If you have selected either the attribute names that reference "supOrgId", the is in condition will be the only option. This is to ensure authorization using Workday Supervisory Orgs works as expected.
-
Enter the desired Attribute value.
-
Leave the Active checkbox selected to have your rule take effect as soon as it is added.
-
Finally, click on the Add button to save the Group Authorization entry you just created.
Rule Attributes
You can select from the following attributes depending on which institution you are affiliated with:
- costCenterId (UW only)
- The identifier of the cost center associated with an employee's job. Example: CC001234.
- empCatCode (UW only)
- A code representing the employee's category. Common values include:
- FA - Faculty
- AS - Academic Staff and University Staff
- SH - Student Hourly
- ET - Employee in Training
- eppn
- Stands for eduPersonPrincipalName, a unique identifier for a user within an institution. Example: bbadger@wisc.edu.
- group (FVTC only)
- Used exclusively by Fox Valley Technical College KB. Example: Staff.
- isMemberOf
- Specifies group memberships, typically managed through services like Grouper or Manifest. Example: uw:org:doit_user_services:demo_internal_kb.
- supOrgId AND empCatCode, OR eppn (UW only)
- A combination rule requiring a match on both the supervisory organization ID(s) and the employee category code(s), or specific eppn(s). Example: SO00001234, AS, bbadger@wisc.edu - The user must belong to organization SO00001234 and be part of the Academic or University Staff category, or their eppn is bbadger@wisc.edu. The eppn values are optional.
- supOrgId OR eppn (UW only)
- A combination rule allowing a match on either the supervisory organization ID or specific eppn(s). Example: SO00001234, bbadger@wisc.edu - The user qualifies if they are part of SO00001234 or if their eppn is bbadger@wisc.edu. The eppn values are optional.
- uiucEduHomeDeptCode (UIUC only)
- A department code representing a user's affiliation at the University of Illinois Urbana-Champaign. Example: 9-A.
-
The Manifest service is recommended for UW-Madison KB groups who wish to provide access based on Workday data (i.e. Sup Orgs and/or Cost Centers) or student affiliation data. For information on setting up and configuring a Manifest group for use with the KB, please see KB User's Guide - Using Manifest to Authorize Users for the KB.
- If you would like to authorize individuals based on employee affiliation data and are unsure of what values to use, we recommend reaching out to your HR department. For UW users, the KB Team can also help verify what values appear for specific individuals.
-
Shibboleth attributes may be used for some data that is not covered by Manifest, though uses are more limited.
Note: For institutions outside of UW-Madison, additional work must be performed to map a specific Shibboleth attribute to the KB for use with Group Authorization. Please contact kb-team@doit.wisc.edu to request a new attribute.
The examples below demonstrate different attributes used for Group Authorization.
- The
isMemberOfattribute grants members of the "uw:org:doit_user_services:demo_internal_kb" Manifest group authorization. - The
eppn(eduPersonPrincipalName) attribute grants authorization to the user "lscheide@wisc.edu".

Updating Group Authorization Scope
Updating an existing Group Authorization rule and changing the Scope dropdown from Document specific to Internal site will result in the following alert:

Note that updating a Group Authorization rule's scope to Internal site will remove all document specific read and write access restrictions associated with that rule. If this is not the intended outcome, click OK to dismiss the popup and change the Scope dropdown back to Document specific.
If you wish to experiment with Group Authorization rules but do not wish to remove document specific restrictions, consider changing the attribute name, condition, and value instead, or create a new rule entirely.
Deleting Group Authorization Rules
To delete a Group Authorization Rule, click the Delete button corresponding the the desired rule. A dialog window will popup confirming you would like to delete this rule. Note that deleting a Group Authorization rule will remove all read and write restrictions associated with it.

Click OK to confirm the deletion.
Other Considerations
-
When a user stops meeting the criteria for a rule (e.g. the user gets another position or leaves your institution entirely) they will lose access to your Internal KB site and/or the documents they were being authorized for.
-
There is no limit to the number of Group Authorization rules that can be created for a single KB space.
-
There is no conflict if a user who has been manually entered into the Users tab of the KB Admin Tools is also a member of an Authorized Group. Any elevated permissions set via the Existing Users list will be honored.
-
There may be occasion for a KB group admin or author to collaborate with a member of an Authorized Group who is a content expert. However, if that individual is not in the Users list, they will be unable to access the KB Admin Tools to view draft (In Progress or In Review) documents. To remedy this, you may create a privately shared link to share one or many unpublished documents with a member of an Authorized Group. Should it be more practical for the content expert to edit the document, the KB group admin need only add the user to the KB.